Encryption with Keys.pub
Disclaimer: Keys.pub has not been audited as of June 7th 2020 for it’s cryptographic robustness so use it at your own risk. I recommend testing it with unimportant documents/messages.
Cryptography is all around us in the Internet. The process of fetching this blog page uses the HTTPS protocol which incorporates Transport Layer Security (TLS, formerly SSL), whose algorithm includes key exchanges between your browser and the server this blog is hosted on.
We’ll be going over Keys.pub, software that is striving to make the creation and usability of cryptographic keys as user friendly as possible. It borrows many ideas and technologies from Keybase.io, which is a small company that was recently bought by the video conferencing software company, Zoom, in order to improve its cryptography implementations.
Due to the uncertain future of Keybase.io, I ran across the Keys.pub project and believe it’ll one day be a worthy successor to Keybase.io
Scenario
Let’s say Barret wants to send a message, [m], to Tifa.
(B)arret [m]
|
|
|
(T)ifa
The problem is that Barret wants to send it without anyone else reading it since it’s a secret. Barret and Tifa both decide to try out the application Keys.pub They install the software on their computers. The first thing it asks Barret is to create a password. This password is to unlock the Keys.pub application and access his keychain.
The keychain is what will hold Barret’s public/private key(s), which he’ll generate next, as well as other functionality within the Keys.pub app. He’ll have to type this in for every new session.
Key Generation
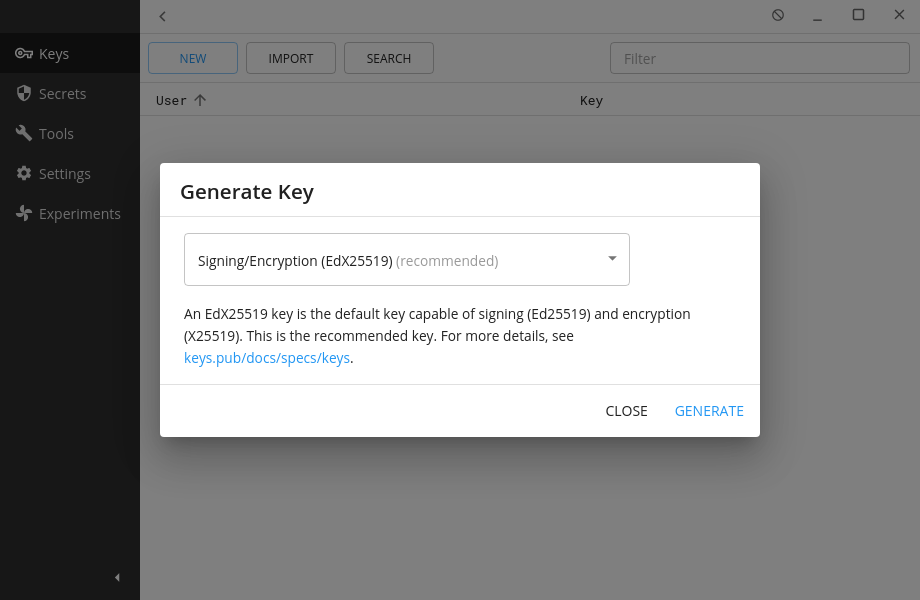 After creating the password (or by clicking “New” in keys sub-menu), the app will prompt to generate a key. Since Barret would like to sign and encrypt messages/payloads, he sticks with the default choice and clicks “Generate”.
After creating the password (or by clicking “New” in keys sub-menu), the app will prompt to generate a key. Since Barret would like to sign and encrypt messages/payloads, he sticks with the default choice and clicks “Generate”.
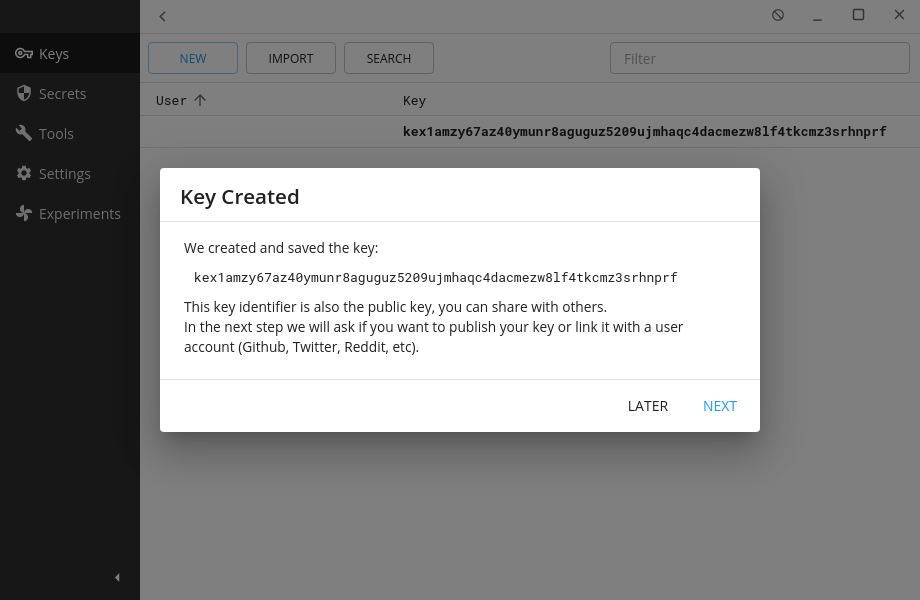
Barret gets a confirmation screen with his public key displaying on it. It’s also added in the “keys” sub-menu and is bold to show he has the private key.
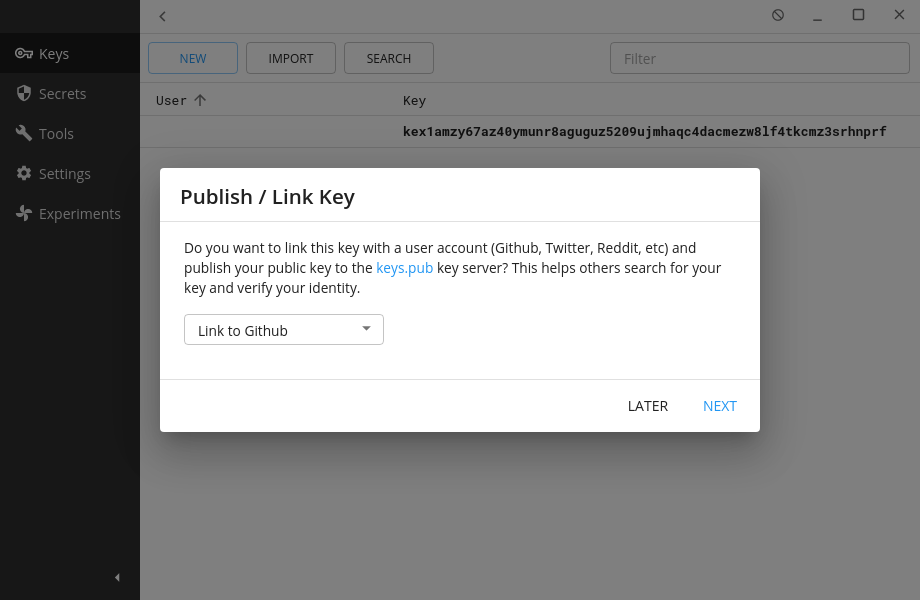
The app gives him the choice to publish/link the key. This is one of the main features of Keys.pub, which allows others to search for your key via Keys.pub or through one of the supported sites. Associating your public key to these sites/services serves as proof that you’re in control of them. For example, you can see mine here for my website.
For now, Barret chooses to skip this by pressing “later”.
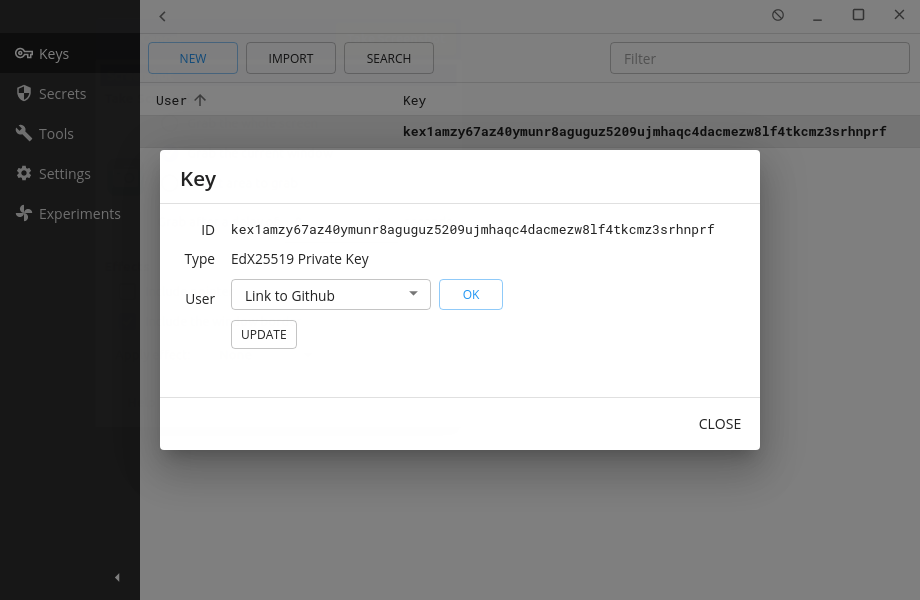
He clicks on his new public key within the “keys” sub-menu and notes down the public key, kex1amzy67az40ymunr8aguguz5209ujmhaqc4dacmezw8lf4tkcmz3srhnprf, to give to Tifa later.
Key Exchange
Both Tifa and Barret are good to exchange keys.
(B) [m]
b_priv_k (****)
b_pub_k (kex1a...)
|
|
|
(T)
t_priv_k (****)
t_pub_k (kex13...)
They exchange their public keys remotely or in-person to ensure integrity of the keys. Their private keys should never be shared with anyone.
(B) [m]
b_priv_k (****)
b_pub_k (kex1a...)
t_pub_k (kex13...)
|
|
|
(T)
t_priv_k (****)
t_pub_k (kex13...)
b_pub_k (kex1a...)
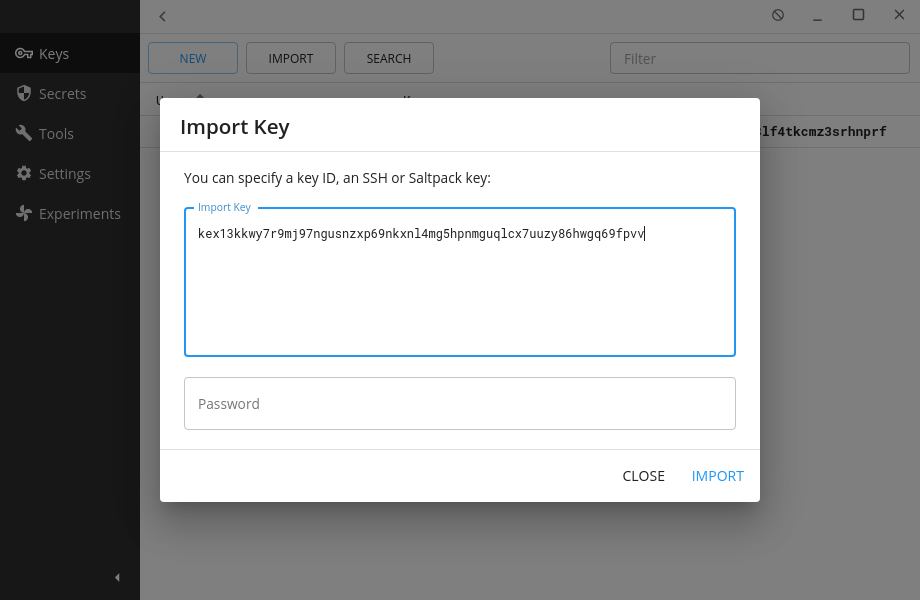
Both Barret and Tifa add the public keys manually to their Keys.pub client applications. Note that they could have also fetched it from other avenues if they published them, such as my website example.
Message Encryption and Decryption
Going back to Barret and Tifa’s situation: Barret goes to the Tools->Encrypt option, selects Tifa’s public key address as the “To” field, selects his key in the “Signed by” so that she knows it’s him (otherwise it’s anonymous), plugs in the message [m] as the payload, and the app automatically encrypts it as he types. If a file was chosen, the encrypted file would output in the same directory as the original.
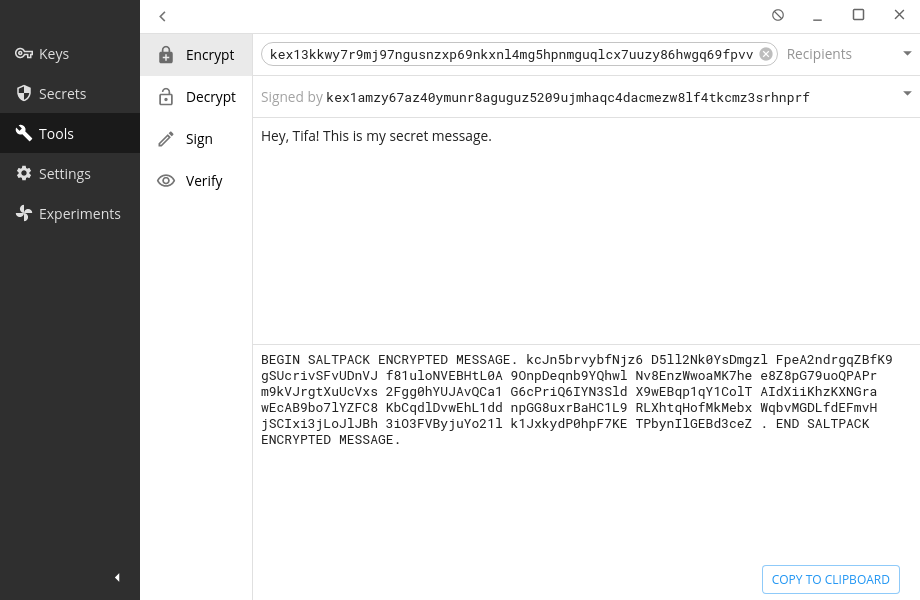
Barret sends this encrypted message [em] over to Tifa through any remote channel considering it’s encrypted and should be safe from tampering.
(B) [m] -> [em]
b_priv_k (****)
b_pub_k (kex1a...)
t_pub_k (kex13...)
|
|
|
(T) [em]
t_priv_k (****)
t_pub_k (kex13...)
b_pub_k (kex1a...)
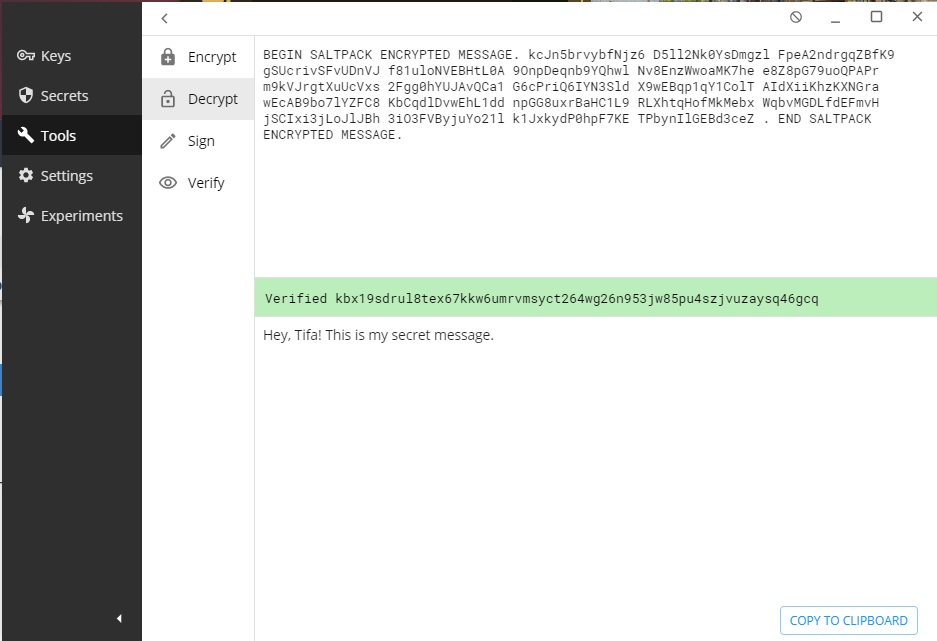
Tifa then types in the message from her Keys.pub application within the “Decrypt” sub-menu option, and she sees the plaintext message along with verification that her friend Barret sent it.
Why use this at all?
After all this, it may seem like a hassle to send simple encrypted messages between friends. Why not just use applications that state they do this in the first place?
The answer has to do with trust. How much do you trust the applications you use? Has it been audited by a third party company to validate it’s claims? Is the code open and available for it? Can you be assured 100% that the installed app you have on your phone or computer hasn’t been tampered with?
Using applications like Keys.pub can help get rid of the middle-man dependency on the cryptography, or at the least add an additional layer of encryption to your sent messages/files. This may not be worth the effort to go through, but imagine being in the shoes of a whistle blower or sending payloads that include sensitive data like bank routing or social security numbers.
Just think of it as a tool and know you have the option of using it if needed. Or just treat it like a toy technology to get a basic understanding of how a modern day marvel (key-exchange cryptography) works!
Other features
Keys.pub seems like it’s improving as time goes on, and it has some neat tricks up its sleeve, such as a wormhole tunnel to move files between computers. If you have questions about any of them feel free to shoot me a message and I’d be happy to walk through it with you.